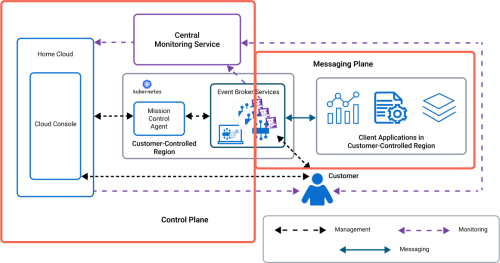
Management, monitoring, and messaging data are the types of data that flow through advanced event mesh for SAP Integration Suite. Each of these types of data take separate and well-defined paths. Logically, advanced event mesh is split into two data planes called the control plane (for management and monitoring data) and a messaging plane (for messaging data). For more information, see Control Plane Data and Messaging Plane Data.
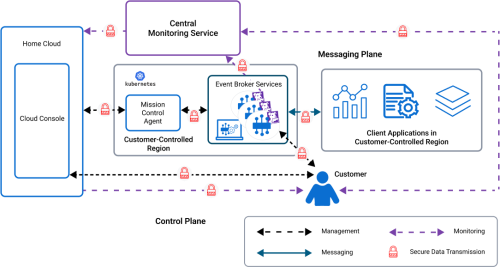
All data is secure and encrypted while stationary or in transit. For more information about data encryption, see Encryption.
The following diagram shows how the planes logically look in a typical deployment:
There is a clear separation between the control plane data [management and monitoring (metadata and logs) data] and the messaging plane [messaging data (events, messages, files, any artifacts that are part of event payload)]. The diagram shows the event broker services within both planes in a Customer-Controlled Region as an example, but the separation of control plane and messaging plane data is the same in any type of deployment.
The diagram also shows a Kubernetes clusters and depicts how the Mission Control Agent handles management data between the event broker services and Home Cloud. This architecture keeps the management/monitoring data separate from the messaging data. For information about the various data flows, see Data Flows within a Customer Environment.
One important aspect to consider regarding messaging data is the sovereignty of the data. This comes down to the where the data resides in a geographical location. Since the advanced event mesh platform can be geographically diverse, it's a good idea to consider this as part of your overall security and data strategy. To address this, you can deploy to a Dedicated Region based on geography. For more information, see Data Sovereignty.
Data Flows within a Customer Environment
The data involved in a deployment of event broker services can be categorized into these types:
- Management Data
- Management data is sent between the Mission Control Agent, Home Cloud, and event broker services. Management data includes configuration information for event broker services and metadata that is sent back to SAP through secure ports. For more information, see Control Plane Data.
- Monitoring Data
- Monitoring data (statistics and event broker logs) are sent to a central monitoring service (Datadog) through secure ports. Transmission of monitoring data is via secure HTTP. Datadog agents use SEMP-based calls to collect statistics and logs from the event broker services. In most cases, monitoring data is one-way, but for users that use dashboards in Datadog, the monitoring data is configurable via a connection – hence it is shown as two-way data flow. For more information, see Control Plane Data.
- Messaging Data
- Messaging data (which includes events, payloads of messages) refers to the information between the event broker services and the publishing and subscribing client applications. No customer data leaves the customer environment if the client applications connect from within the same VPC/VNet. Messaging data is resident within the customer's perimeter (in their VPC/VNet). For more information, see Messaging Plane Data.
- Any messages transmitted between client applications and the event broker services are secured using encryption, by default. Data stored in the VPC/VNet is encrypted. For about data encryption, see Encryption.
Control Plane Data
The control plane consists of both management and monitoring data. Management data uses secure SEMP calls to perform tasks such as configuring event broker services, configuring certificates for advanced event mesh, and communicating with the Mission Control Agent. Monitoring data encompasses gather monitoring statistics and logs, which is done using Datadog agents on each event broker (this means there are three Datadog agents in a High-Availability service). The statistics and logs that Datadog agents collect use SEMPv2 based interfaces.
The Control Plane uses secure HTTPS calls to make API calls to cloud vendors to configure DNS records and manage compute instances (EC2 Instances, Virtual Machines, etc.).
The management data from the control plane travels within a secured communication channel with the Home Cloud and the central monitoring service. SAP uses this data to manage and monitor the health of the event broker services. Management data comes from various functions, including:
- User interactions with the Cloud Console to create and manage event broker services. The creation of an event broker service is handled ultimately by the Mission Control Agent deployed in the same VPC/VNet.
- User interactions from the Broker Manager, which directly connects to an event broker service.
- Collection of metadata and logs that are sent to the central monitoring service. The monitoring information is sent between Home Cloud and the user.
Information from event broker services is collected to monitor the health of the event broker services. For information on the logs collected, see Event Broker Service Logs.
Messaging Plane Data
The messaging plane contains the events, data, and payload of the messages that are transported between the event broker services and client applications. Messaging data exists in its own plane and is not accessible from the control plane.
- For more information, see Event Broker Services.
Encryption
All data in advanced event mesh is encrypted. Encryption occurs to data that is in transit (transmitted via events and messages) and at rest (stored in persistent storage for queues). Any logs, management data, or statistics collected are also encrypted.
Encryption is a consideration for data in transit and when it's stored. Sensitive data is treated with additional care on advanced event mesh.
Encryption of Data in Transit
Data that is transmitted between the client applications (both publishers and subscribers) and the event broker services is secure. By default, the messaging data that is brokered by the event broker services between publishers (producers) and subscribers (consumers) is secured in the following manner:
- event broker services use messaging protocols and ports that are secured with TLS 1.2 (default)
- non-encrypted protocols (plain-text ports) are available for configuration to support legacy applications, but are disabled by default; plain-text, non-encrypted protocols are not recommended for production environments
- certificates are regularly updated and whenever Security Advisory concerns require resolution
Data at Rest
Data at rest is any data stored on message spools (virtual, persistent, and external persistent storage). By default, SAP applies encryption to all persistent data at rest. We apply encryption to all online and backup disks to ensure data remains protected. We use server-side encryption for storage services (S3, databases, etc.).
In Public Regions and Dedicated Regions, we encrypt data at rest using AES-256 and the Key Management Service (KMS) of your chosen cloud provider. SAP uses the following principles when storing data:
-
Encrypt by default; encryption is not optional.
-
Use cloud vendor KMS to encrypt disks using AES-256 encryption.
-
Encrypt sensitive data on the Control Plane before storage using AES-256 encryption.
-
Encrypted disks store messaging data reside in the same cloud region as the event broker service.
Self-Managed Encryption Keys for Dedicated Regions
SAP supports self-managed encryption keys for some Dedicated Region cloud providers. With a self-managed encryption key, you control access to your data and can revoke the key at any time. SAP currently supports the following self-managed encryption keys:
When choosing to encrypt the data at rest in your event broker service's message spools, you must provide the self-managed key to SAP.
Encryption of Sensitive Data
Sensitive data, like passwords are hashed using BCrypt and credentials are encrypted using AES-256.
Data Sovereignty
Data sovereignty refers to the laws and governance that the collection and storage of data adheres to, which is based on the nation where the data resides or is collected. Since the data is separated into two planes, the sovereignty of the data is as follows:
-
Messaging data remains with the event broker services, it adheres to the laws of the geographical region where the event broker services are deployed. The sovereignty of messaging data is a common use case for security regulations and this can be decided by the customer.
To address messaging data sovereignty requirements, SAP recommends the event broker services be installed in a private network (e.g., Kubernetes cluster in a VPC/VNet) in the region where the data must be. For example, if the data must stay within a particular geographical region, deploy the event broker services in that geographical region using private network. For more information about VPC/VNet isolation, see VPC/VNet Isolation.
-
Management data comprises of logs, statistics, and metadata. The metadata is utilized and stored by the Home Cloud and Cloud Console (including Event Portal, Insights, and Cluster Manager), which is referred to as the regional site. A third-party central monitoring service (Datadog) collects and stores operational logs, metrics, and statistics that are used for central monitoring from the Home Cloud.
At this time, both the Home Cloud and central monitoring service are stored in the United States of America and therefore adhere to the laws in the United States of America.