Audit logs provide records of user activity for security and compliance. You can view, monitor, and track the sequence of the following activities in advanced event mesh:
- IAM operation, such as user login activities
- User management activities, such as user activation or role changes
- Event broker service life-cycle events, such as event broker service creation, upgrades, or deletion
- Operations or activities that occur to Micro-Integrations
- Approval or denial of event access requests.
You can modify the scope of the audit log entries that are displayed by applying filters and customizing the columns. You can also download the audit logs to your workstation. The audit logs are retained in the console for six months; records older than six months are automatically deleted.
Audit logs are collected for an account in advanced event mesh and not used for the monitoring of event broker services. If you are looking for logs that contain information about event broker services, you can do one of the following:
- Use Insights, which collects metrics and provides useful visualizations of event broker services. For more information, see Insights.
- Forward the logs from the event broker service to a server or an external log monitoring system that you control. For more information, see Forwarding Logs to an External System.
For more information about audit logs, see Using Audit Logs and System Logs
For information about retrieving the logs programmatically with the REST API for advanced event mesh, see Managing Audit Logs with the SAP Integration Suite, Advanced Event Mesh REST API.
Who Can Access the Audit Logs?
Administrators
Administrators can access the audit logs for the whole organization. They can view and track actions performed by all users and understand "who did what, where, and when?" within the enterprise account. Administrators can download the audit logs of any user within the organization to their workstation.
All users
All non-administrator users can access only their own audit logs. Individual users can monitor and track their own audit logs, and download them to their workstation.
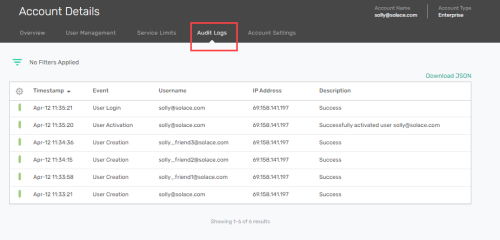
Viewing Audit Logs
You can view the audit logs in the Account Details section in the console. You can also filter the audit logs based on fitler criteria that you provide.
To access the audit logs:
- Log in to the Cloud Console if you haven't already.
- On the navigation bar, click User & Account
 and select Account Details.
and select Account Details. - Select the Audit Logs tab and you will see the default list view that shows:
- the date and time of the occurrence
- the unique event ID for each entry
- the event category (IAM or Service).
- the type of event
- the information of the user who performed the activity
- the IP address of the device used to connect to the console
- the time taken to complete the activity
Use the filter to change the scope of the entries to display.
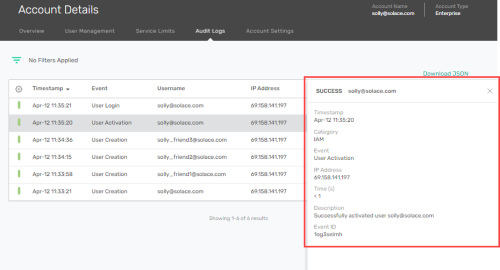
- Click an audit log entry to display additional description. The information panel contains description to help you make the most of your audit log data.
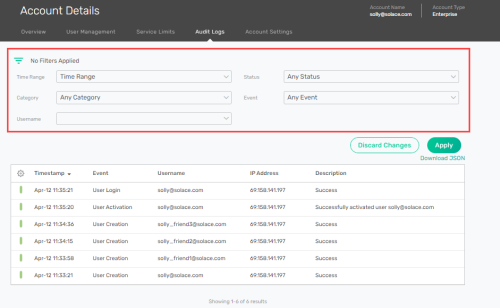
Filtering Audit Logs
All the audit log entries for the past week are displayed by default. Administrators can see the audit log entries of all the users within the enterprise account. Using the filter, you can specify the fields that are displayed on the UI.
To apply filters, do the following:
- Log in to the Cloud Console if you haven't already.
- On the navigation bar, click User & Account
 and select Account Details.
and select Account Details. - Select the Audit Logs tab and click Show Filters
 to expand the options.
to expand the options. - From the available options, you can apply the following filters:
- Time Range—Filter the logs based on the time range which can be Last hour, Last 12 hours, Last Day, Last Week, or Last Month.
- Category—Filter the logs based on IAM or Service activities. You must select one of the following options to enable filter options in the Event field:
- SERVICE—Service lifecycle and management activities that occur to the event broker services in the account.
- IAM—User access activities that occur to the account.
- EVENT_ACCESS_REQUEST—User activities for access requests.
- Username—Filter the logs based on a specific user in the account. Only users with the Administrator role can filter using this option.
- Status—Filter the logs based on the status of the activity (Successful, Failed, or In Progress).
- Event—Filter the logs based on the type of activity selected. The options in this list are accessible only after you select an option in the Category list.
- Once you've set the filters, click Apply to filter the logs; otherwise click Discard Changes.
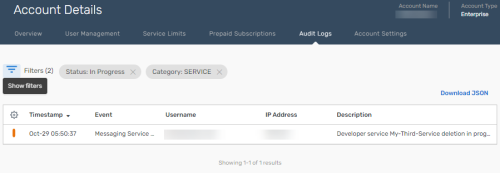
You can repeat steps 4-5 to further filter the logs or click filter criteria to remove it as shown below.
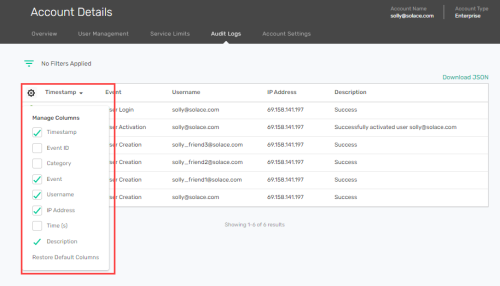
Managing Column List View
Use the Manage Columns ![]() to add or remove columns from the audit log entries.
to add or remove columns from the audit log entries.
- Log in to the Cloud Console if you haven't already.
- On the navigation bar, click User & Account
 and select Account Details.
and select Account Details. - Select the Audit Logs tab, and then on the table, click the Manage Columns
 . This will open a menu with the list of fields that are available for you to select to appear in the table.
. This will open a menu with the list of fields that are available for you to select to appear in the table. - Select or deselect the check box to show or hide a column from the table, respectively. The columns you choose are automatically saved.
Downloading Audit Logs
You can download the audit logs as a JSON file. The downloaded file contains all the records that match the criteria selected. If no filter criteria is selected, all the entries for the last week are downloaded by default.
To download a filtered audit log, do the following:
- Log in to the Cloud Console if you haven't already.
- On the navigation bar, click User & Account
 and select Account Details.
and select Account Details. - Select the Audit Logs tab.
- (Optional) Apply filters to the audit logs. See Filtering Audit Logs for the steps.
- Click Download JSON.
The JSON file will be downloaded to your computer.
Audit Log Reference in SAP Integration Suite, Advanced Event Mesh
The following are the audit logs you may see:
The term messaging services in the audit logs refer to event broker services.
| Category | Event Type | Description |
|---|---|---|
| IAM | UNKNOWN | The event type could not be determined |
| EVENT_ACCESS_REQUEST | EVENT_ACCESS_REQUEST_APPROVED | Event Access Request Approved |
| EVENT_ACCESS_REQUEST | EVENT_ACCESS_REQUEST_DECLINED | Event Access Request Declined |
| IAM | UNKNOWN | The event type could not be determined |
| IAM | LOGIN | User Login |
| IAM | LOGOUT | User Logout |
| IAM | USER_CREATION | User Creation |
| IAM | USER_DELETION | User Deletion |
| IAM | USER_ACTIVATION | User Activation |
| IAM | PASSWORD_RESET | User Password Reset |
| IAM | PASSWORD_CHANGE | User Password Change |
| IAM | USER_DELETE_ORGANIZATION | User Organization Deletion |
| IAM | USER_CREATE_ORGANIZATION | User Organization Creation |
| IAM | ENVIRONMENT_CREATE | Environment Creation |
| IAM | ENVIRONMENT_UPDATE | Environment Update |
| IAM | ENVIRONMENT_DELETE | Environment Delete |
| SERVICE | SERVICE_CREATE | Messaging Service Creation |
| SERVICE | SERVICE_CLONE | Messaging Service Clone |
| SERVICE | SERVICE_DELETE | Messaging Service Deletion |
| SERVICE | SERVICE_UPDATE | Messaging Service Configuration Change |
| SERVICE | SERVICE_FAILOVER | Messaging Service Active Node Switch |
| SERVICE | SERVICE_UPGRADE | Messaging Service Upgrade |
| SERVICE | SERVICE_SCALEUP | Messaging Service Scale Up |
| SERVICE | SERVICE_SHOW_PASSWORD | Unmask password on Manage Service Settings |
| SERVICE | SERVICE_SEMP_PASSWORD_CHANGE | Messaging Service SEMP Password Change |
| SERVICE | SERVICE_SEMP_USER_CHANGE | Messaging Service SEMP User Change |
| SERVICE | SERVICE_LIMIT_CHANGE_REQUEST | Messaging Service Limit Change Request |